Network Firewall vs. WAF: Why You Probably Need Both (Not Just One)
If you ask an IT professional what the most basic building block of cybersecurity is, they will almost certainly say "a firewall."
But in today’s complex digital landscape, the term "firewall" has become dangerously vague.
Many businesses assume that because they have a firewall installed at their network perimeter, their web applications are secure. This assumption is often the root cause of major data breaches.
The reality is that the traditional network firewall protecting your office perimeter is fundamentally different from the tool needed to protect your e-commerce site or customer portal. The latter requires a Web Application Firewall (WAF).
Understanding the difference between a traditional firewall and a WAF isn't just semantic pedantry; it’s the difference between locking your front door and locking the safe inside your house.
Here is a breakdown of the battle: WAF vs. Traditional Firewall.
1. The Fundamental Definitions (The "Bouncer" Analogy)
To understand the difference, we need to look at what these tools were designed to protect.
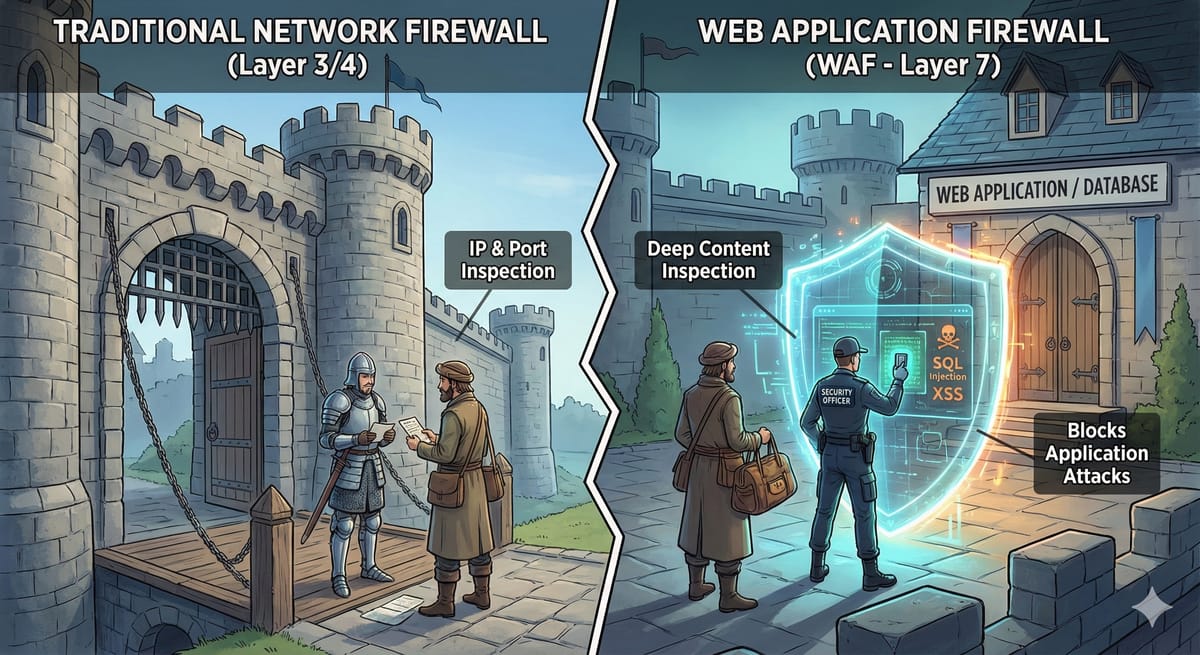
The Traditional Firewall (Network Firewall) A traditional firewall is designed to protect the perimeter of a network. Think of it as the security guard at the front gate of an office building. Their job is to check IDs. They look at who is coming in (IP address) and which door they want to use (Port). If your name isn't on the list, or you are trying to use a blocked entrance, you don't get in.
The Web Application Firewall (WAF) A WAF is specialized. It doesn’t care about the building perimeter; it cares specifically about your web applications (your website, your APIs, your mobile app backend).
If the traditional firewall is the guard at the front gate, the WAF is the specialized bodyguard standing right next to the VIP inside the building. The WAF doesn't just check IDs; it listens to the conversation. It analyzes the actual data packets being sent to your web application to ensure they don't contain malicious instructions.
2. Key Differences: Layer 3/4 vs. Layer 7
This is where we get slightly technical, but stay with us—this is the most important part. The difference lies in the OSI Model (the layers of network communication).
Traditional Firewalls handle Layers 3 and 4 (Network and Transport)
They make decisions based on:
- Source IP: Where is this coming from?
- Destination IP: Where is it going?
- Port/Protocol: Is this traffic trying to use port 80 (HTTP) or port 22 (SSH)?
Crucially, a network firewall is "blind" to the content of the traffic. If you have port 80 (web traffic) open, the firewall lets everything through that port, whether it's a legitimate customer browsing a product or a hacker sending a malicious script.
WAFs handle Layer 7 (Application)
A WAF operates at the very top layer. It decrypts and inspects the actual HTTP/S requests and responses. It understands how web applications work. It looks for patterns that indicate an attack against the logic of the application itself.
3. When to Use Which: Real-World Scenarios
You can't use a hammer to screw in a lightbulb. You need the right tool for the job.
When a Traditional Firewall wins:
- Blocking unauthorized access: Preventing someone outside your company from trying to connect to your internal file servers via SSH or RDP.
- Network segmentation: Ensuring the marketing department's computers cannot talk to the highly secure finance department's servers.
When a WAF is essential:
- SQL Injection (SQLi) Protection: A hacker tries to input database commands into your website's login form to dump your user database. A network firewall sees this as normal web traffic and lets it through. A WAF sees the malicious SQL code and blocks it instantly.
- API Security: Your mobile app talks to your backend via APIs. A WAF inspects these API calls to ensure someone isn't trying to manipulate the data structure to gain access they shouldn't have.
- OWASP Top 10 Threats: WAFs are specifically designed to mitigate the top threats listed by the Open Web Application Security Project, such as Cross-Site Scripting (XSS) and broken authentication.
4. Real-World Examples: The DDoS Distinction
Even when dealing with the same type of attack, like a Distributed Denial of Service (DDoS), these tools handle things differently.
- Traditional Firewall DDoS Protection: Excellent at stopping "volumetric" attacks. If a botnet tries to overwhelm your network pipe with 100Gbps of junk UDP traffic, the network firewall is your first line of defense to drop that traffic before it clogs your lines.
- WAF DDoS Protection: Excellent at stopping "application-layer" (Layer 7) DDoS attacks. These are sneakier. The attacker doesn't flood the network; instead, they send thousands of slow, complex search queries to your website that exhaust your server's CPU and RAM, causing it to crash. Only a WAF can detect this pattern.
5. The Verdict: Can They Work Together?
Yes. Absolutely. In fact, they must work together.
This is the core principle of a "Defense-in-Depth" strategy. You never rely on a single security control.
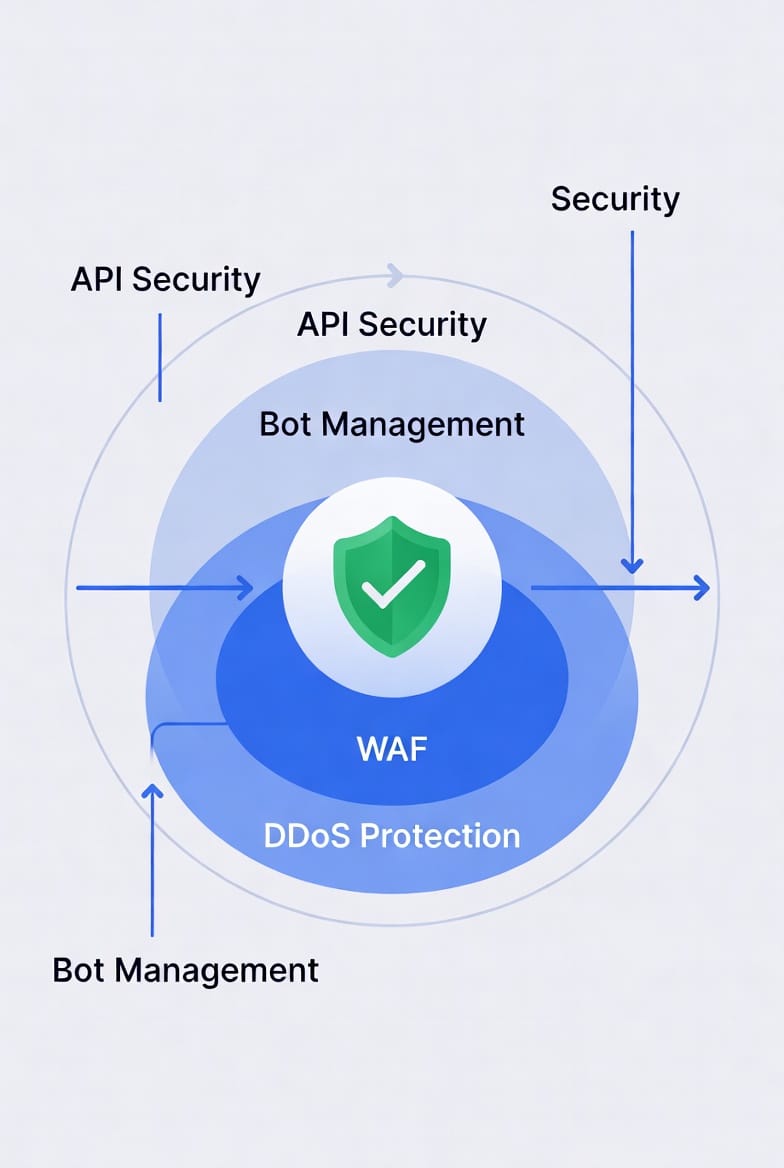
A robust security architecture looks like an onion. The traditional network firewall is the outer skin, filtering out network noise and unauthorized connections. The WAF is an inner layer, sitting in front of your web servers, heavily scrutinizing the traffic that the network firewall already allowed through.
If you only have a traditional firewall, your applications are wide open to hacking. If you only have a WAF, your underlying network infrastructure is exposed.
The Takeaway
Don't fall into the trap of thinking "I bought a firewall, so I'm secure."
If you are running any public-facing web application, e-commerce site, or customer portal, a traditional network firewall is not enough. You need the specialized, Layer 7 intelligence of a Web Application Firewall to stop the threats that target your data directly.